There are so many great examples and lessons to be learned from the cyber attack that caused the Ukrainian power outage on December 23rd. Kim Zetter of Wired has one of the best articles on this if you want the public version of the full story to date.
The remote control of the HMI while the operator was watching had some sizzle. As did the wiping of the computers in the Control Center and compromising the UPS to keep the Control Center dark when the power went out. However the really nasty and novel attack in the ICS space was loading bad firmware on the Serial-To-Ethernet converters. The bad firmware overwrote the firmware upload function so you could not recover these devices. It likely required a hardware replacement and redeployment that extended the outage of the SCADA system.
If you have ever played with a PLC or other embedded device in the lab and tried to load your own test firmware on a PLC you can appreciate the ease of this attack. We have accidentally bricked some PLC cards in our labs trying to create proof of concept EtherNet/IP malware and other attack code.
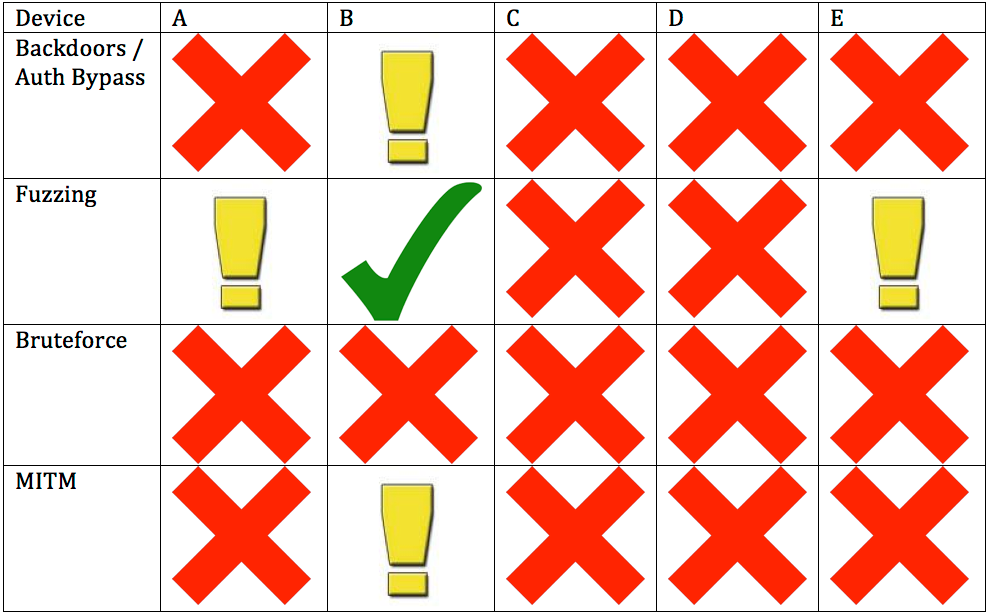
This attack was clever, but not unforeseen. The first row of the chart in the original Project Basecamp results back in January 2012 was testing for this specific attack, and it was discussed in earlier S4 papers by Daniel Peck and myself. And maybe it isn’t so clever because all the attacker is doing is overwriting good firmware with garbage.
The other foreshadowing was Reid’s Basecamp for Serial Converters post in October of 2015. These little devices are widespread in ICS and get minimal attention, but they are in the communication path and are necessary for communicating with serial PLC’s, RTU’s and other embedded devices. In fact, many asset owners believe that since there PLC’s are serial the risk of a cyber attack is minimal. If this was ever true it is certainly less true now that this attack technique is proven.