
What Problem Are You Solving?
The application for S4x26 Proof of Concept (POC) Pavilion begins with a simple question. What problem is your product or service solving? The POC Pavilion will have a highly realistic asset owner OT environment. (You can watch the reveal of Pavilion provider, system,...
Possible Isn’t A Compelling Argument
In a recent LinkedIn post Andrew Ginter made the case that legal liability is an argument for investing in cybersecurity. That those responsible for managing risk, and cybersecurity in particular, should put in place "reasonable" security controls to reduce legal...
Why Little Secure Coding Interest In OT?
Most years we include a secure coding session on S4's Stage 2 Technical Deep Dives. This year it was Colin Breck's: It's Not As Simple As "Use A Memory Safe Language". The session drew a small audience, even though it was given a prominent spot in the agenda. Those...

Rating Past OT Security Acquisitions
It's been over five years now since the OT Asset Inventory and Detection market sorted itself out. The top tier has changed little. The increased acceptance of cloud-based solutions has helped Armis join original top tier vendors Claroty, Dragos, and Nozomi. There...

False and True: You Can’t Protect What You Don’t Know
False One of the most common OT Security mantras this decade is “You Can’t Protect What You Don’t Know”. Those who say this are almost always saying you can't protect your OT environment without a detailed and accurate OT cyber asset inventory. This is...

What’s Next For DHS / CISA In OT Security?
I've had the chance to interview the last three leaders of DHS's OT security efforts at S4 (only missing out on Seán Paul McGurk). For good or bad, the message has been consistent. Emphasis on information sharing, public / private partnership, new .gov organizational...

Anecdotes Are Not Data
A large part of OT Security marketing is based around anecdotes. Some anecdotes are real. This small water utility was hacked and a tank overflowed. This manufacturer had ransomware and had to shut down certain factory operations for three days. This rail system was...
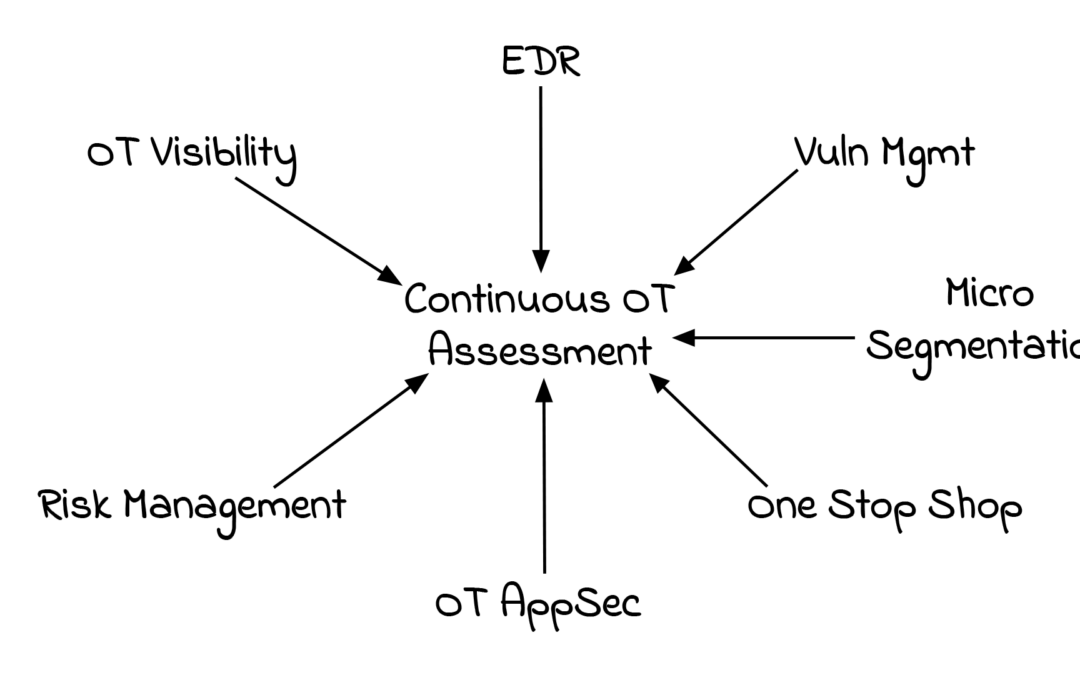
Frenos: Is “Continuous and Autonomous OT Assessment” A Sustainable Product Category?
Frenos is hot. They won the Datatribe Challenge, and then raised $3.88M in a seed round led by Datatribe. They got Rob Lee on their Advisory Board. And the founders have hired some well known talent in the space such as Tony Turner and Vivek Ponnada. There hasn't been...

“Discovering ICS Vulns Is So Yesterday”
Love this comment from Bryan Owen on one of my posts. Discovering ICS vulns is so yesterday, discovering implants is the new, new thing. In observation, there needs to be more emphasis and coverage on discovered implants... otherwise sponsors of defensive programs are...

Mythology and Metrics
OT Security needs metrics. I originally wrote more metrics, but we have almost no metrics. We includes asset owners, governments, vendors, industry groups, ... We shouldn't be funding anything that doesn't include a hypothesis and a metric that will provide data that...
GET DALE'S ICS SECURITY NEWS & NOTES EMAIL EVERY FRIDAY
Article Archive By Year
Article Archive By Category
UPCOMING EVENTS
OTCEP ... 29 - 30 July 2025 in Singapore
One of the best OT Security events in Asia. Dale will be playing cowboy that week and will unfortunately miss it. Most of the rest of the OTCEP panel will be there on stage.
S4x26 ... 23 - 27 February 2026 in Miami South Beach
Save the date for S4x26. For the biggest and most future focused on ICS Security Event ... and likely our last time in Miami South Beach.
