One of the nastiest aspects of the attack on the Ukrainian Electric Distribution System was bricking the Moxa Ethernet-to-Serial gateways. Industry insiders have known these little devices were a security problem. Reid goes over the timeline when it was disclosed to Moxa prior to Ukraine, their public promise to fix it by August 2016, and the still awaited fix.
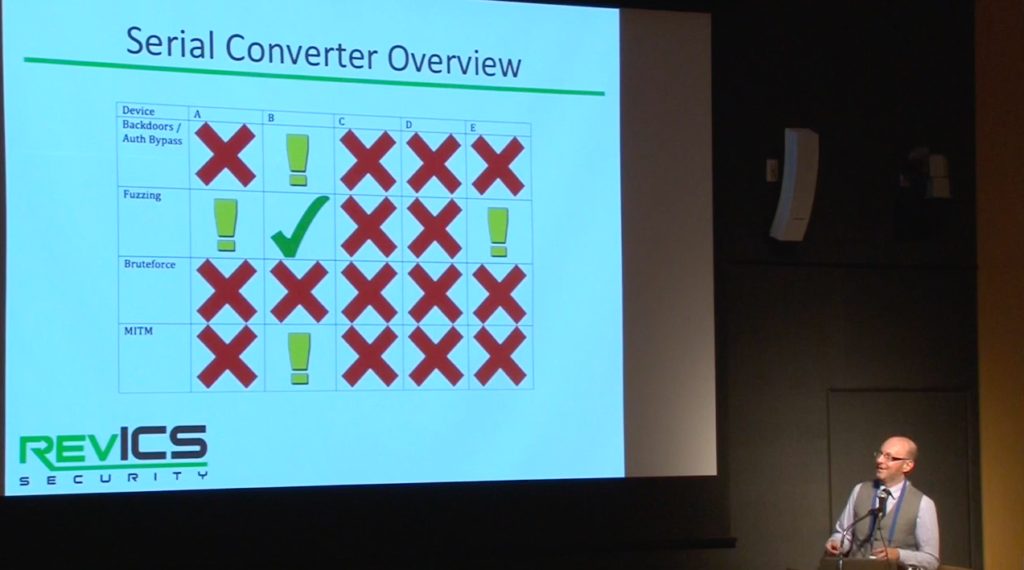
As you can tell by the thumbnail picture, Ethernet-to-Serial gateways commonly used in SCADA and other ICS are easily compromised in a variety of ways. Reid Wightman dives into the details in models from Moxa, Digi, Lantronix and GridConnect. It’s likely most other models are just as bad.
The technical aspects of this session, while detailed, hardly taxed Reid’s skills and are no way showing off elite ICS offensive techniques. Rather it’s the typical insecure by design, insecure proprietary protocols, and poor coding and design practices across a class of ICS equipment. We actually would not include a session like this in Stage 2: Technical Deep Dives in Miami Beach. It’s too basic.
The main reasons to watch this video are:
- The classic vendor responses to researcher disclosed vulnerabilities. Everything from no response, unmet promises, and the classic the device was never meant to be secure … live with it … we won’t tell people it is insecure and will continue to sell it.
- To think about how this quite simple, widely deployed device is so perfectly positioned for attackers. It is required for monitoring and control communications to serial PLC’s, RTU’s and controllers. And it is like the printer on the corporate network. It is a great place to hide attack code and achieve persistence even after the computers in the ICS are cleaned. From the attackers perspective an insecure device that has no cyber maintenance or monitoring is very appealing.