What Does The Attack on a Schneider Electric Triconex Safety System Mean for the ICS Community?
In the last seven days, I’ve posted the S4x18 videos from Schneider Electric, Mandiant, Dragos and the Langner/Tudor comments on TRITON, a failed attack on a Triconex safety system purported to be in the Middle East. You can see these on the ICS Attacks playlist on the S4 Events YouTube channel. After all this information plus the initial papers from Mandiant and Dragos, here are the three important things to take from this incident.
1) Schneider Electric set the new standard for ICS vendor response when a vendor’s system is attacked.
It’s hard not to compare Siemens’ response to Stuxnet with Schneider’s response to Triton. Siemens was pure denial and marketing spin; and not just in the early weeks, but literally for years. Stuxnet occurred over 7 years ago, and Siemens would likely do much better responding in 2018.
Schneider Electric deserves huge credit for their forthright approach to the Triton malware.
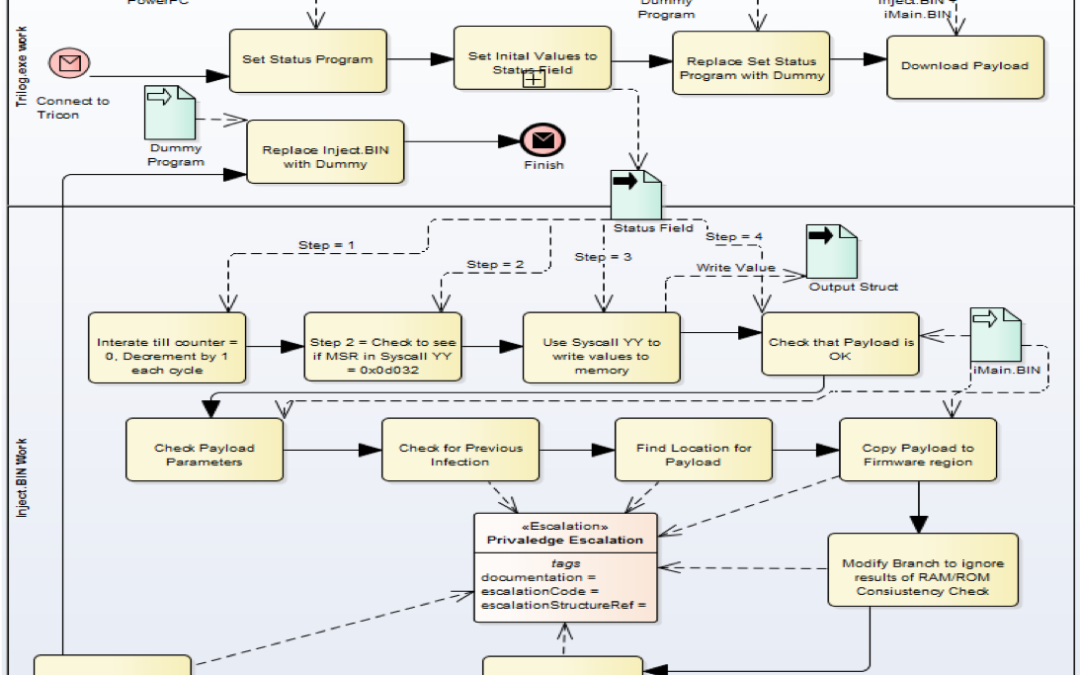
- They actually fixed the bug in the malware and got it to run so they could determine exactly what it does.
- They identified and disclosed the details of the attack, a controller vulnerability, and areas where their safety controller, and likely most safety controllers, need to be improved.
- They released to customers a tool to detect and remove the malware.
The one thing remaining is to verify which versions of their controller are vulnerable to this attack if the initial checks to find and attack a specific installation are removed.
Other ICS vendors should be ready to perform as well, or even better. The sky did not fall when Schneider Electric made the difficult decision to break precedent and do this. They were applauded by the industry.
2) The attacker end goal is likely known by the asset owner that was attacked.
First, great job and appreciation to the asset owner that allowed Schneider Electric and Mandiant to release details on the attack. I know the media and many in industry are clamoring to know who was attacked. I hope this does not become public. We need asset owners to feel comfortable they can share information without getting outed and getting the negative blowback.
Ralph Langner makes a good point in the Closing Panel that safety controllers have a specific purpose. While the attack payload to modify how the safety controller performs it’s safety function was not recovered, the asset owner can look at what that safety controller was doing and narrow down with confidence why a skilled attacker would want the ability to modify the safety logic in that controller.
3) Increased integration of Safety / Protection systems and networks with ICS is a mistake.
Many vendors that sell both ICS and Safety/Protection systems have been promoting integration of these systems. Have them on the same network or even have cards in the same backplane. If your ICS is hacked, this should not provide the attacker with any jumping off point to get to the Safety or Protection system.
The general public still does not know, how the attacker got to the Safety Engineering Workstation. If it was from the ICS or another network, this was a significant design flaw, although it would have followed many vendors’ recommendations. It could also have been physically brought in accidentally or intentionally by an insider.
Either way, asset owners should realize the attackers now know that Safety and Protection systems can be attacked, and they are an important target if significant damage is desired, as opposed to just an outage.
As a final note, Schneider Electric and others have stated that Triton was developed and deployed by a highly skilled and resourced nation state. The nation state is a leap, in my opinion. A small highly skilled team could have accomplished this given access to the EWS and controller software. I could create a few of those teams just from S4 attendees. And the effort failed, which indicates the testing was not adequate. A nation state might take more care in sending untested code, and ultimately failed code, into a safety system. They couldn’t control the results.