Solving a problem typically begins with awareness that there is a problem. Back at S4x12 a group of researchers under the Project Basecamp banner demonstrated that most PLC’s (Purdue Level 1 devices) were both insecure by design and ridden with exploitable bugs, as well how an attacker could leverage these issues. Nine years later I believe the issue is known in the ICS security community, even if it is just beginning to be solved.
Similarly, ICSsec pioneer Joe Weiss has been on a content blitz the last three years pointing out that Purdue Level 0 devices, sensors and actuators, do not have any security. Primarily with the example that false process sensor data could be presented to the control system. He has asserted that the ICS security community does not know this, most recently in a post SANS ICS Security Summit article.
there appeared to be a general acceptance that Level 0,1 devices were uncompromised, authenticated, and correct. That is wrong
Joe and I had a back and forth on LinkedIn on whether this misconception was present in the S4 audience, SANS ICS Security Summit audience, and ICS security community in general. My belief was lack of security at Levels 0 and 1 was common knowledge in the ICSsec community and the only disagreements are the prioritization of addressing this issue amongst the large number of issues and how it should be addressed. We tried to answer this disagreement with a poll.
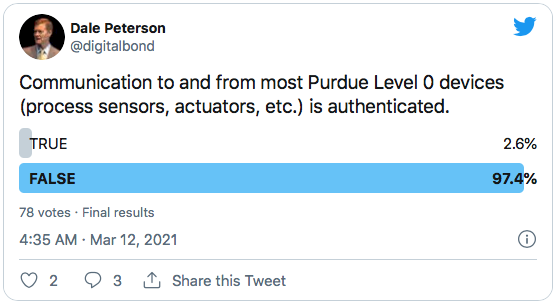
The same poll in my Friday Newsletter had 147 responses with 98% answering False. It is likely that there is some overlap in the respondents to the two polls. 97% is clear evidence that the ICS security community understands there is not security at Level 0, and I’m certain they also know it is exceedingly rare at Level 1.
This does not mean there is no awareness problem. Security professionals coming in from the IT security world often do not know and are surprised to learn this. The bigger problem is when asset owner executives are unaware of this because it can lead to spending a lot of money and effort on good practice security controls that have little impact on risk. It is incumbent on Operations and OT Security to inform executives of risks and the best risk reduction options.
What I’m still uncertain of is how well known the insecure-by-design Level 0/1 problem is in the ICS involved engineering community. I’d like to believe that similar to the ICS security community this is common knowledge. I don’t have an audience of engineers who are not involved in ICS security. Any readers with the right audience want to run a poll?
Next Week: The Solution To Level 0 / Level 1 Lack Of Security Problem
Subscribe to my ICS Security: Friday News & Notes email.

