We have resolved the issue on whether the ICS security community knows that almost all Purdue Reference Model Level 0 and Level 1 devices, and the protocols that communicate with them, lack authentication. They know this. The next question is what to do about it from an OT / ICS risk management perspective. I’ll break the answer into two parts. This article will cover efficient risk reduction prioritization, and next week’s article will cover the recommended security controls.
In a perfect world with unlimited resources, all Level 0 and Level 1 devices would have a set of security controls. New devices would come with the security controls and deployed devices would be upgraded. Since resources are limited and ICS cybersecurity risk reduction options are plentiful, deciding the priority of risk reduction actions is important.
This is similar to evaluating the risk reduction provided in applying security patches in ICS. It is a good security practice to apply all security patches that mitigate vulnerabilities. However as shown in ICS-Patch: What To Patch When In ICS, there is a large variance in the risk reduction achieved in various asset / patch pairs. The small percentage of patches that result in significant risk reduction should be applied asap, and the large percentage of patches that result in almost no risk reduction should be deferred and applied primarily when needed to keep the product in a supported state.
Similar to ICS-Patch, a decision tree is a good way to look at the prioritization of securing Level 0 and Level 1 devices, see diagram below.
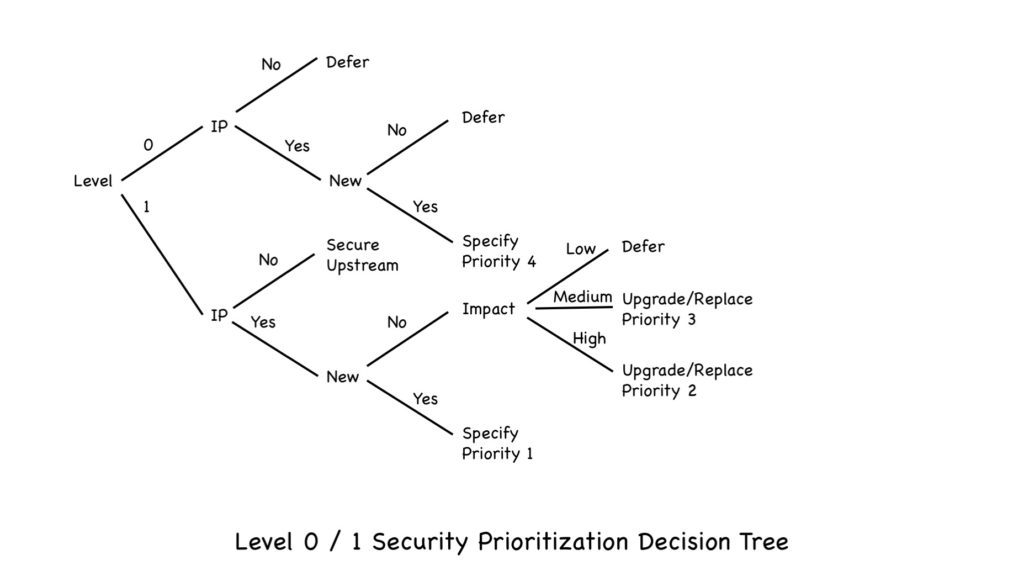
Exposure is the most important factor in determining ICS risk reduction. It was the first decision point in ICS-Patch, and it’s the first decision point in determining the risk reduction achieved in securing Level 0 and Level 1 devices. How easy will it be for an attacker to access, and therefore be able to compromise, the device or the communication to and from the device?
Factor: Exposure… Level 0 or Level 1?
Securing Level 1 provides a leveraged security point with significantly more efficient risk reduction than securing Level 0. The PLC, RTU, Controller or other device at Level 1 typically communicates with many sensors and actuators. It can be a perimeter security device that stops or limits attacks from reaching the Level 0 device from untrusted networks.
Falsified or bad sensor data is often given as a reason to secure Level 0. Yes, a compromised Level 0 sensor could send back incorrect data that could lead to an incorrect and consequential control action or inaction. However, a compromised Level 1 device connected to that sensor could also provide falsified or bad sensor data for that sensor. The compromised Level 1 device could additionally falsify sensor data for all other sensors it is connected to, send rogue commands to all actuators it is connected to, and alter any of its process logic.
Prioritizing Level 1 security over Level 0 security is similar to prioritizing a firewall to limit enterprise and Internet communication from reaching the ICS over securing the Level 1 devices.
Factor: Exposure… Ethernet Port / IP Stack?
If a Level 0 or Level 1 device has an Ethernet port and an IP protocol stack, it is much more likely to be attacked and compromised through cyber means than if it does not.
There are two reasons for this. First, the IP stack makes it much easier to route attacks to the device. As we know the air gap is almost always a myth. IP based networks are connected to share information, and this provides a potential attack path to the device if it has an IP address. Second, most of the attack tools, as well as almost all of the attacks and attack attempts to date have tried to compromise ICS cyber assets via this interface.
Can a Level 0 or Level 1 device with an “analog” or “serial” interface be accessed? Yes. It could be reached from an IP network through a serial-to-ethernet gateway, and this gateway is a better, again from an efficient risk reduction standpoint, place to put cybersecurity. This is the location where you should apply your security controls, whether it be through an industrial security gateway or other means.
And yes, a serial Level 0 device can be accessed by physically connecting to the serial network. This often, but not always, requires close physical proximity to the device and physical attacks on the device or process are typically easier than cyber attacks with this access.
This will be a contentious point with some, and I’m not arguing against security in all devices. The point is we will achieve greater risk reduction by securing the devices in each level that have an IP address than securing those that do not have an IP address, and they should be prioritized.
Factor: New or Legacy
I used the Will Rogers quote “if you find yourself in a hole, stop digging” in a recent article on the legacy system problem. Any new devices with an IP address should have security. At Level 1 there are a small, but growing list of devices with the basic security functions that will be described in next week’s article.
If the choices available for purchase lack security then you should either insure there is an acceptable upgrade path to add security or plan on a much shorter lifecycle than usual, such as 2 to 5 years rather than decades.
Which only leaves the question of what to do with legacy devices with an IP address.
Factor: Impact
Legacy Level 0 devices with an IP address fall into the defer category. Even looking 5 years out it is hard to find a case where an efficient risk reduction approach would lead to replacing or adding on security to these devices.
Legacy Level 1 devices with an IP address should be upgraded or replaced in the order of the impact of compromise of their availability and integrity. In general, Level 1 devices that are involved in control, changing the physical component, should be prioritized over Level 1 devices that are connected solely to sensors. There are a number of ways to detect bad sensor data. That said, there are examples where bad sensor data would be difficult to detect and would lead to high consequence actions, and this would lead to PLC’s associated with these sensors being prioritized.
Level 0 and Level 1 Security’s Position In An ICS Security Program
The decision tree in this article prioritizes the order to add security in the Level 0 / Level 1 category to address the insecure by design problem. It does not describe when this issue should be addressed in relation to all of the other potential ICS cyber risk reduction activities. It is easy to identify activities that provide more and less risk reduction than addressing the Level 0 or Level 1 security issue. Some examples:
Greater Risk Reduction Than Addressing Level 0/1 Insecure By Design
- Enterprise / ICS Security Perimeter
- Two-factor authentication for remote access
- Ability to recover minimum required ICS cyber assets
- Large scale consequence reduction
Less Risk Reduction Than Addressing Level 0/1 Insecure By Design
- Majority of security patching inside the ICS security perimeter (Defer category in ICS-Patch)
- Individual Operator accounts in a 24/7 control room
- ICS application security controls at Level 2.
Next Week: Appropriate Security Controls for Level 0 and Level 1
Subscribe to my ICS Security: Friday News & Notes email.

