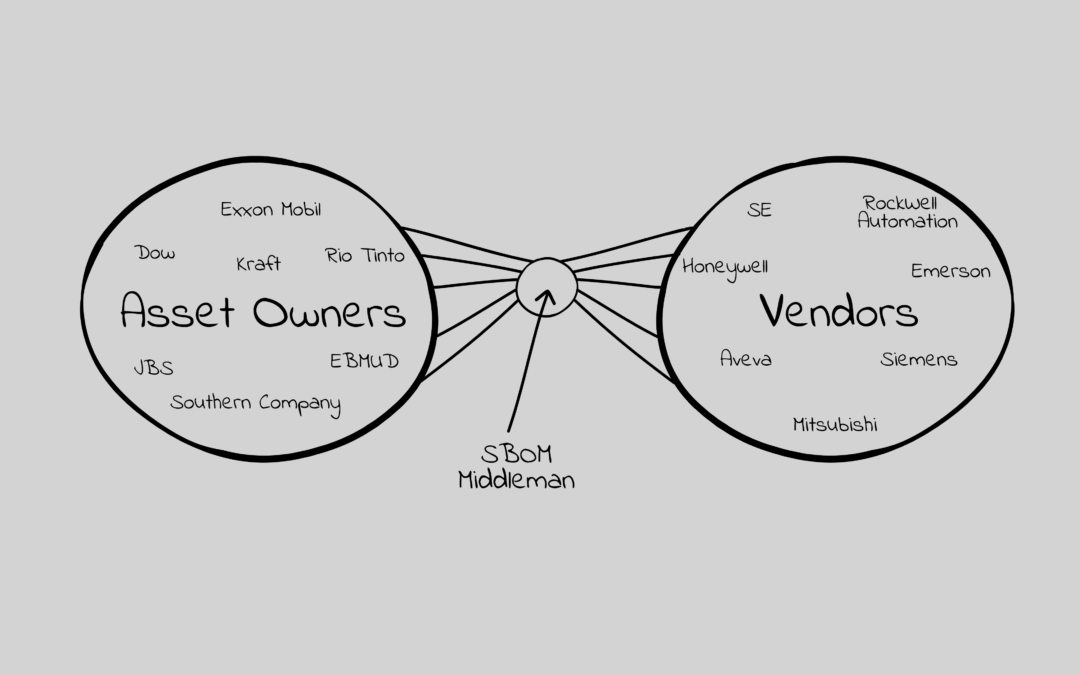
The image in this article is what I believe will determine winners and losers in the SBOM marketplace. Who will develop and implement the best business model of mediating the need for vendors to provide and asset owners to access SBOMs with VEXies. Here is my reasoning.
- The Creation Of SBOM’s Will Not Be A Differentiator (Most who try will succeed)
I don’t want to imply it is easy, but the ability to take software and firmware and create a software bill of materials (SBOM) is straightforward. It is the price of entry into the market. It is being done well by most of the competitors in the space today. It will not be a differentiator.
We will be able to validate or refute this assertion at the S4x23 SBOM Challenge. More on this later, but I’m excited about the team we have who will run this and the approach they are taking. My expectation is we will see, yes, SBOM products can generate highly accurate SBOMs.
2. Accepting A Feed Of Which Vulns Are Exploitable Will Not Be A Differentiator
A product’s SBOM ingredients may have a large number of published vulnerabilities, but most of these won’t be directly exploitable. The number I hear most often is ~10% of the vulnerabilities in a SBOM are directly exploitable. VEX and other acronym laden efforts are creating ways to provide a machine readable feed that says a product is, or is not, susceptible to a direct exploit of a SBOM identified vulnerability. I haven’t seen a term for this yet and will refer to it as VEXie until one is coined.
Another minimum requirement to play in this product segment will be the ability to import these VEXie feeds and tell the owner/operator what vulns in the SBOM require attention. This also will be tested in the S4x23 SBOM Challenge.
3. The Vendor Tool Market Is Not THE Big Market
Today the SBOM solutions are already valuable to the ICS vendor, and any vendor providing a product with software/firmware, in creating SBOMs to help with product development, product maintenance, and SBOM demanding customers. While this wouldn’t be a small, sub $10M annual sales market, it is not the big market. In addition, if this was THE market there would be substantial pricing pressure. Perhaps even a race to the bottom.
The counterargument could be a subscription based model or even a service based model where the SBOM vendor creates and maintains the SBOMs. This starts to look like the right half of the image in this article.
The market you want is one that can service the much larger asset owner / ICS customer space.
4. Most Asset Owners Will Not Want To Have A SBOM Feed From Each Vendor
Today, most ICS asset owners have difficulty creating and maintaining an asset inventory, as well as meeting the security patching policy they define. Even when the security patching policy is limited to the ICS apps, OS and little else. Adding in the volume of information in SBOMs and VEXies will be daunting.
Now imagine needing access to these SBOMs and ever changing vulnerability status, even if only used in incident response and specific questions (do I have SolarWinds?). Asset owners likely have 10’s of vendors, at least, that they would need to connect to, import, store, query, etc. The level of effort vs. value provided is minimal.
Even if the ICS asset inventory vendors integrate and enrich the inventory with SBOM information, they still need to get it. If I was to argue against my own analysis, the possibility of these ICS asset inventory tools gathering SBOM with VEXie information from the large number of vendors is a competitive model. I don’t believe that the ICS vendors will want to deal with this for a variety of reasons.
5. Most Vendors Will Not Want To Support SBOM Requests From Each Customer
Admittedly, this could be another part of the support portal. It’s a lot of work, unlikely to lead to additional support revenue (unlikely there would be a SBOM support surcharge), and not the core business the vendor is in.
Could a Schneider Electric, Siemens, or Honeywell do this? Sure. They also could invest in or spin off a company to do this. In these early days, it would be powerful if Siemens and Schneider Electric, or any two large companies, worked with a SBOM startup to provide a SBOM with VEXie for all of their products to licensed customers. An initial partnership / investment with one vendor is less appealing as it could discourage other large vendors from joining in.
These partnerships and investments is something I’ll be watching closely to understand the competitive landscape.
6. There Are Multiple Ways To Add Value In The Middle
If, and it’s a big if, a SBOM middleman can be responsible for gathering all of the SBOMs with VEXies that an asset owner would want then:
- they could charge the asset owner a monthly subscription (recurring revenue) to meet their future cyber hygiene requirement to have and potential actually use SBOMs
- they could charge the vendor a monthly subscription (per product?, product line?, organization wide) to provide this service to their customers
- they could add asset owner services to this information such as: prioritized patching guidance, sector specific patching guidance, product security ratings, secondary testing of VEXie results, threat intel, …
- they could add vendor services to this information such as: volume and types of queries to understand security conscious customer base and secondary testing of VEXie results
Conclusion: The winners of the ICS SBOM Product Segment will be the companies that best occupy a SBOM middleman position. This will be determined by
- who is most effective at creating the early and key partnership and use by large vendors and asset owners,
- who can create an effective mediation offering and business model, and
- who will have the resources and will to invest strongly in the sales, marketing and partnerships while the revenue remains relatively low for 2 – 3 years.
Next Week: What Will Determine Near Term SBOM Vendor Wins?