We have been preparing some new and interesting challenges for the S4 CTF this year, and I think that players will have a lot of fun with what we have in the works. We have a number of nice challenges that involve breaking and entering into our ‘Killer Robot Factory’ (players from last year’s CTF may remember a few flags associated with the poor Killer Robots — for all of the pain that they cause humanity, they don’t secure their network very well).
One of last year’s challenges was to find the product order code for a feeder management relay. This relay was used to control a breaker that could disconnect the poor Killer Robots from their electric mains.
While we have a few SEL-751As in our test lab, we though that putting one in harm’s way for the CTF might be a bit of a stretch. Even ‘good’ industrial equipment such as that made by SEL tends not to deal very well with many simultaneous users. That, and if people messed with the equipment, it could be a pain to restore to working condition.
Instead, we built a SEL emulator (or honeypot) in Python using the cmd2 library. The emulator is kind-of-sort-of good, and provides a sort-of-realistic simulation of an SEL relay — enough to trick CTF players, anyway.
We wanted the challenge to have a wireless aspect. We thought that setting up a bluetooth to serial gateway that was ‘accidentally’ left connected to the feeder management relay would be fun.
SEL actually makes two models of bluetooth to serial adapter, called to SEL-2924 and SEL-2925. (Note: we have never assessed either device for security, although we definitely do not recommend using such devices as a permanent installation on any critical infrastructure — the Bluetooth standard has numerous security issues and the chipsets involved are very difficult to secure from a supply-chain perspective).
Labs was on a very unrelated engagement when we learned what SEL’s converter devices have inside of them. For our research project, we purchased a few Roving Networks RN-42 bluetooth-serial adapters. While most Bluetooth-Serial chips use an AT-style command set for configuration, the Roving Networks models had a different firmware that used the characters ‘$$$’ to enter a special configuration/command mode.
Looking for other devices which used this special command-mode entry, we stumbled upon the SEL-2924 and SEL-2925. Most of the actual configuration commands for these adapters overlap with the Roving Networks firmware, so we imagine that they are very closely related — most likely the same actual chip, with a very similar firmware. Of note, the RN-42 devices provides little in terms of securing it from a malicious firmware update…see for example this article, which shows how to extract an RN-42 firmware and write it into another module.
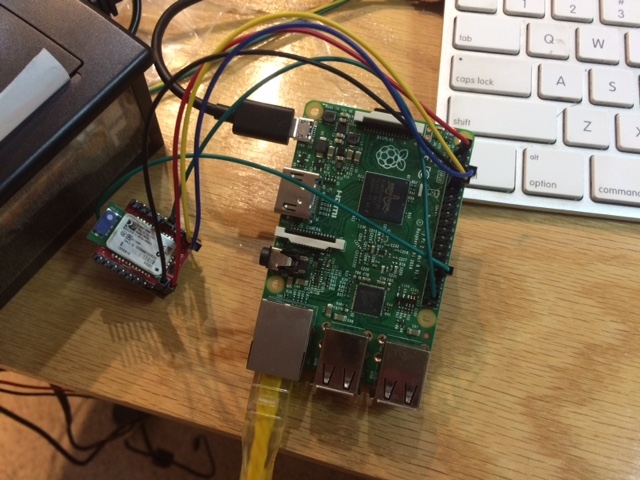
Anyway, the adapter that we purchased was from Sparkfun Electronics, and since it is so similar to the SEL device, we decided to use it in our CTF. We connected it up to a Raspberry Pi, which would serve as the fake SEL relay.
If you have ever written a serial command-line interface before, you can probably guess what happened next. It is a little annoying writing such things, especially when the serial port may be connected to by several different people back-to-back. You have to reset the state of the serial port between users connecting, otherwise one user may go through the authentication steps and leave the device ‘logged in’, making the challenge easier to solve for the next team. So, how to do that?
Fortunately the RN-42 bluetooth-serial adapter has a few GPIO pins that can tell you about the state of the bluetooth connection. A quick read of the RN-42 user manual reveals that PIO2 changes state when a user connects and disconnects.

We connect the RN-42’s PIO2 to two digital inputs on the Raspberry Pi to track the state of the user. This way we can automatically log a team out if they left the console session logged in.
Next was feeding data from the serial port to our Python program. We could have done something pretty with pyserial, but it turns out that Python’s serial libraries are kind of gross. Chiefly, we couldn’t make Python echo back asterisk characters to the user when they typed in the passwords needed to get access to the relay (well, maybe there is a cute way to do this, but would require re-implementing the cmd2 library we think). This was disappointing, but we glued our Python-based command line interface together with a serial port data shuffler using golang (and, threads!).

Included here is our Golang code for listening to the bluetooth serial port, and our Python code for driving the actually command-line. Note that the cmd2 library has a number of neat commands for executing comand-line programs, and our script doesn’t actually prevent all of them from working; but the Python code could be used as a start of an SEL honeypot, for anyone brave enough to run such a thing. There are many SEL devices that may be found on the Internet, and we often wonder if anyone is trying to do something malicious with these devices.
Code and instructions for recreating this challenge have been uploaded to the Digital Bond github repository.