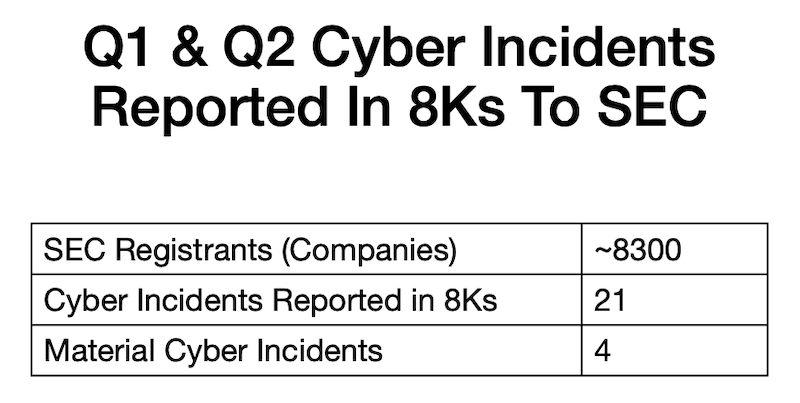
21 Jul 2025 | A Year In OT Security
Predictive maintenance, efficiency studies and controls, security monitoring, and other cloud services can offer real benefits to asset owners. This trend of vendors offering, and asset owners using, cloud services is almost certain to increase. The challenge is to...
14 Jul 2025 | A Year In OT Security
Now that your OT remote access is secured, determine if the allowed remote access is necessary. Ideally user interactive remote access to OT for the purpose of performing control or administration should be rare. If this is the case, consider if it’s feasible to have...
7 Jul 2025 | A Year In OT Security
Most of the targeted, OT specific attacks, where the adversary has lived on the OT for many months, began with a compromise of remote access to OT. The limited OT cyber incident data we have clearly shows that multi-factor authentication (MFA) for OT remote access is...
30 Jun 2025 | A Year In OT Security
De-militarized zones (DMZ), semi-trusted zones, are a common electronic security perimeter good practice. The firewall segmenting IT from the Internet will often have one or more DMZ to limit direct Internet to IT network communication. A web server, database...
23 Jun 2025 | A Year In OT Security
Take the information gathered in Week 24 on your OT electronic security perimeters and evaluate the risk related to each communication allowed through the OT electronic security perimeter. This is typically a rule by rule analysis. If you have a well-documented...