Consequence Based Techniques for ICS Risk Management
This recording is from a panel discussion on understanding and reducing the consequence side of the risk equation (risk = consequence * likelihood). Joining me in this discussion are:
- John Cusimano of aeSolutions and their CyberPHA
- Andy Bochman of INL and their Consequence Driven Cyber Informed Engineering (CCE)
The two gentleman begin by explaining their respective consequence based risk assessment and risk management, and the diagrams they refer to are below.
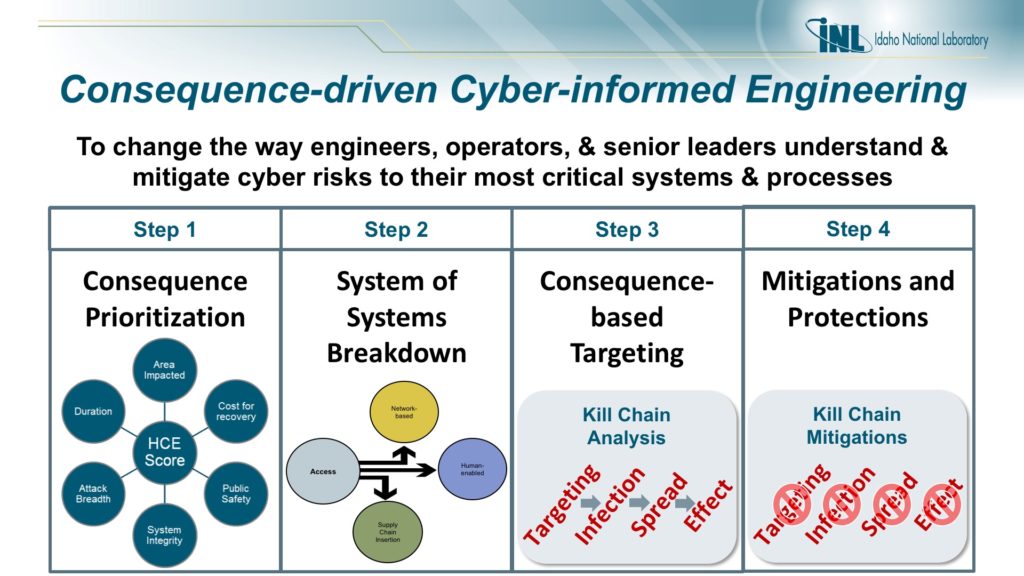
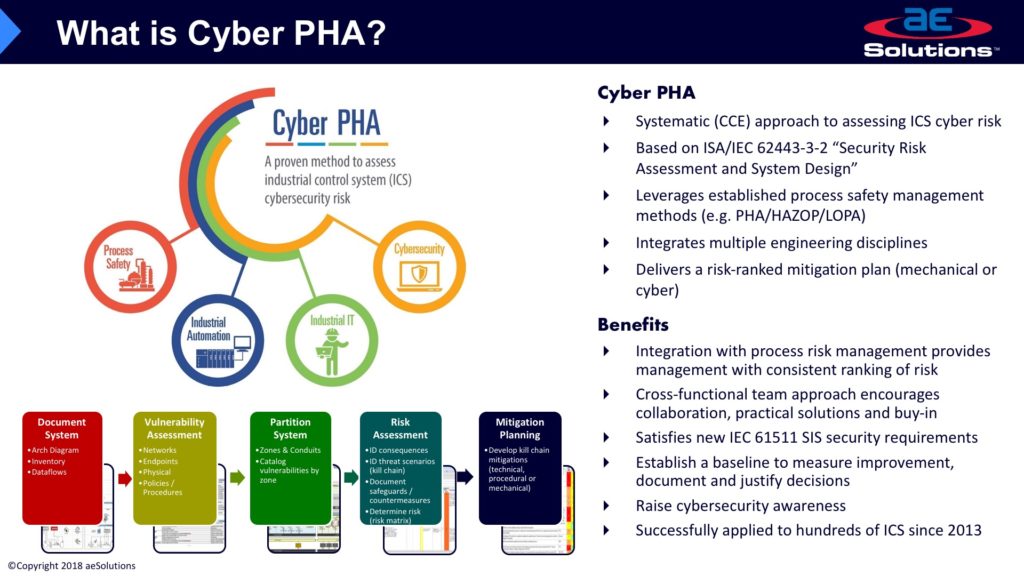
After the initial descriptions we discuss:
- how the two approaches are similar and different?
- how long it takes to perform a CCE or CyberPHA?
- what are some of the novel consequence reduction solutions?
- the difference between disruption and destruction as a consequence?
- will the CyberPHA be integrated into the PHA?
Links
This episode was sponsored by CyberX. Founded by military cyber experts with nation-state expertise defending critical infrastructure, CyberX has developed an end-to-end platform for continuous ICS threat monitoring and risk mitigation.
Check out the 2019 CyberX Global ICS and IIoT Risk Report, the CyberX report on the NIS Directive, and my podcast from last year on the report with Phil Neray.

