Thinking Out Loud …
The ICS Detection market is new and highly competitive as covered in an early article. A question as interesting as who will be the winners in this market, is what the composition and capabilities of the winning solutions will be?
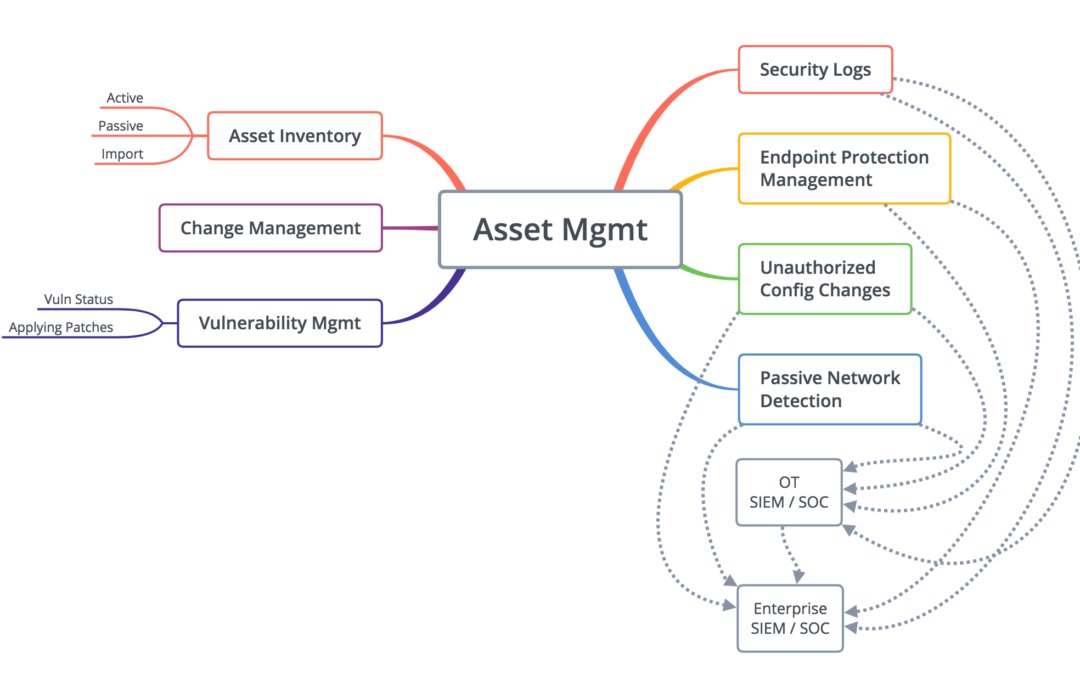
The diagram above lists some, but not all, of the main capabilities that could be included in a solution. You could draw circles around any of these capabilities and create a product offering, even if the areas are not directly connected. The current crop of competitors have solutions with a circle around Passive Network Detection, Passive Asset Inventory (with an increasing number adding Active and Import), and the Vulnerability Management (status only). This is only one possibility and unlikely to be the final winning combination.
I interviewed Ralph Langner for an upcoming Unsolicited Response podcast episode, and he is convinced, and designed his OT-BASE solution around the belief, that Asset Management will be a separate solution from Detection. The communication between the two, primarily Asset Management sending information to the Detection/SIEM/SOC, will be important, but it isn’t necessary to have a unified solution.
The communication between various components within Asset Management and Detection will also be important. For example, there may be an existing Asset Management or Change Management application that doesn’t have an active querying capability that would want the latest Asset Inventory from one of these new products. And many, if not most, of the current competitors in the ICS detection market have strategies on forwarding security event data to a SIEM rather than becoming a SIEM.
If we drill down into the Asset Management solution, there are questions about components. Right now “Vulnerability Management” is one of the most requested features by asset owners, and many of the new solutions are offering and improving their capabilities to identify the current patch status of computers and devices. They are not actually applying the patches. Leaving the question, if the asset owner needs to deploy another solution to deploy the patches that can also tell patch status, and that solution is used in the Enterprise as well, would they want this ICS solution to perform the vulnerability management status function? Or is this an interim state and capability for the offering?
The combination of Asset Management and Detection makes more sense when you look at the configuration monitoring and change control portions. Knowing there was an unauthorized change to PLC logic is an important indicator of a potential cyber incident. PAS has offered a solution with circles around Asset Inventory (active), Change Management, and Unauthorized Configuration Changes (and Vulnerability Management – Status), primarily Asset Management with a bit of Detection.
There is also the question of what combination of capabilities will result in the most defendable and profitable category. It could be a hollow victory to win in a commodity / low margin market. The signature based nature of intrusion detection and prevention solutions and anti-virus led to an equivalency that could similarly occur in the ICS passive solutions as they exist today. Right now it’s a race to support, in depth, a wide range of ICS protocols and devices, but that race has an endpoint or at least a point of significantly diminishing returns. The ability to perform process variable anomaly detection based on proprietary machine learning algorithms could be more sustainable.
We have seen cases, such as Checkpoint for a long time in firewalls, where a superior GUI and user experience was the determining factor. Almost every early user of the detection solutions I talk to 1) raves about the information and visibility they provide and 2) is unsure how they will deal with all that information even in the pilot project. The ICS world is well aware of alarm fatigue, and is just beginning to see the equivalent in the detection realm. Perhaps the winner in the detection market won’t be the most comprehensive solution, but rather the solution that finds the right balance between false negative and false positives and presents the information in the most useful manner for the analyst.
One area that it is less likely to be combined is security controls that fall into the protection category, such as firewalls (enterprise and ICS gateways), application whitelisting, future PLC endpoint protection solutions (wait until you see some S4x19 sessions) and even security in network infrastructure devices. Old timers will remember that Network Associates, Cisco and others have purchased companies in the past with the vision of putting them together under a common security management platform. Customers would love this, but it becomes too difficult and expensive to develop and maintain. In the ICS world we’ve seen the equivalent with Emerson’s Ovation Security Center selecting products and creating an offering. While the idea of a combined service offering under many products exists and is growing, building and selling a combined, manage all your protection from our management application is unlikely.
I realize this article is more questions than answers. And the tough part about making predictions on what the winning solution composition will be is it is likely to be very different in the 1 – 3 year time period then in the 3 – 5 year time period. The competitors have to meet the needs and stay in business during the interim time period by giving the asset owners what they think they want, all the while positioning themselves and architecting the product to excel with the final composition in 3+ years.
The ICS security product business is not easy.