9 Apr 2024 | 2024, Strategy
The barbell strategy is most common in finance and became more widely known after its use in Taleb’s Antifragile. Barbell Strategy: A dual strategy, a combination of two extremes, one safe and one speculative, deemed more robust than a “monomodal” strategy;...

15 Feb 2024 | 2024, Strategy
Note: this article was triggered by a Dragos report and briefing Tuesday on Volt Typhoon (they call it VOLTZITE) and its potential future impact on cyber/physical systems. The real message, the key takeaway on Volt Typhoon for those running critical infrastructure ICS...

16 Nov 2021 | 2021, Strategy
See Part 1 with Levels 1 – 3. I must admit I switched the order of Basic Detection and eliminate High Consequence Events multiple times in writing this article. As always I welcome your comments including your own maturity levels. Maturity Level 4: Basic...

10 Nov 2021 | 2021, Strategy
A reader (Paul) wrote in with the following question: Do you have any recommendations on how to iteratively and pragmatically raise the bar (i.e. security/maturity). The models I’ve seen push asset inventory/visibility and cyber hygiene to the front, which makes...

26 Oct 2021 | 2021, Strategy
Bryan Owen in his OnRamp ICS Cloud Services module described open and closed loop cloud services. Securing open loop cloud services is simple because communications can be limited to pushing ICS data to the cloud. Closed loop cloud services can involve the external...
29 Oct 2019 | 2019, Strategy
Most of the activity in the ICS security product market has been around passive solutions that create asset inventories and detect cyber incidents. It is a bit astounding that the market and solutions will look almost completely different in two to five years than...
14 Feb 2019 | 2019, Strategy
This week we published the S4x19 video on three proposed revisions to the Common Vulnerability Scoring System (CVSS) for ICS vulnerabilities. It’s worth a watch and hopefully it will be one more trigger for ICS-CERT to earn the “ICS” in their title...
3 Jan 2019 | 2019, Strategy
In October 2018, Digital Bond turned 20. I thought before moving on to 2019 and starting our 21st year I’d reminisce a bit and thank the many employees over the past 20 years (see the list at the end of the article). Roger Collins and I started Digital Bond with $75K...
5 Dec 2018 | 2018, Strategy
It’s How Do We Best Build OT Teams & Programs My last post, Best Raw Material for an Operations Technology (OT) Team, received many comments on LinkedIn. A lot of the discussion devolved into the old IT v. OT discussion, partially due to my flippantly...
27 Nov 2018 | 2018, Strategy
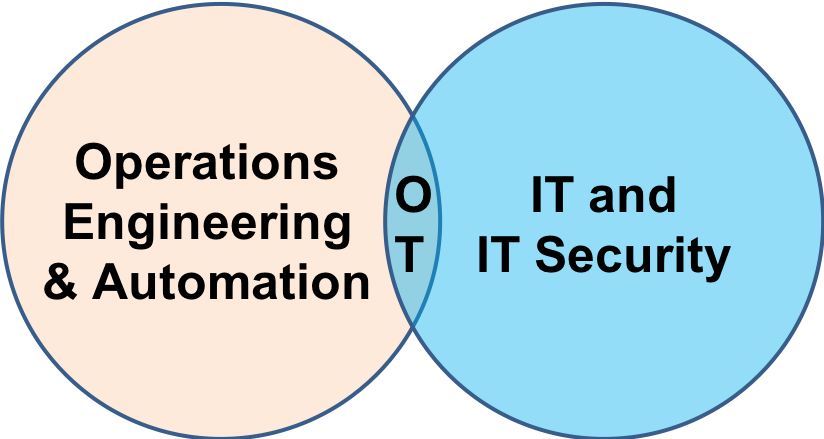
One of the topics we tackled in a panel at the Asia ICS Cyber Security Conference last week in Singapore was how best to grow the Operations Technology (OT) Security workforce. Early in his conference introduction Dan Ehrenreich showed a diagram similar to above with...







