27 Feb 2018 | 2018, Detect, Podcast
The ICS Detection Challenge at S4x18 last January pitted Claroty, Gravwell, Nozomi and Security Matters in a competition to determine who could create the most complete asset inventory and who could do the best job detecting attacks through passive ICS network monitoring only. Dale Peterson and Eric Byres discuss the packets used in the test and analyze the results. What this product category can and cannot do. The last 15 minutes talking about the future of the ICS Detection product category.
20 Feb 2018 | 2018, Podcast
After quickly agreeing that vulnerabilities in medical devices & software are dense, Dale Peterson and Josh Corman discuss where time and money should be spent on improving Medical Sector cybersecurity. Does the find and patch vulns make sense when the vulns are dense? Why does a hospital shut down for a week when a single application has an exploited vuln? How is the FDA doing in forcing change? What can we expect in the future. This and more in this episode.
13 Feb 2018 | 2018, Detect
The Asset Identification and Inventory results from the Challenge showed the potential of these solutions, but also the limitations due to maturity and a passive only approach. Claroty won the Asset Identification phase by identifying the largest number of assets (device type and vendor) with a score of 23, followed by Nozomi and Security Matters with a score of 20. Nozomi clearly provided the most detail in their asset inventory and was the only competitor to identify the key SCADA system. Security Matters did the best in identifying CVE’s for the asset inventory.
11 Feb 2018 | 2018, Detect
The Detection Phase of the ICS Challenge was won narrowly by Claroty (24) over Nozomi Networks (22) and Security Matters (22). Congratulations to the Claroty product and team. The final score was not as interesting as what was detected, what was missed, and conclusions about this product class. This post has five conclusions Dale pulled from the scoresheets and interviews, notes on the scoring methodology and deficiencies, and a chart showing the 19 incidents inserted into the packet capture.

9 Feb 2018 | 2018, Podcast
I had the pleasure of interviewing Dan Geer on the S4x18 Main Stage for 30 minutes. He typically speaks from prepared papers, so an interview is a bit unique, and his papers provided plenty of topics and questions....
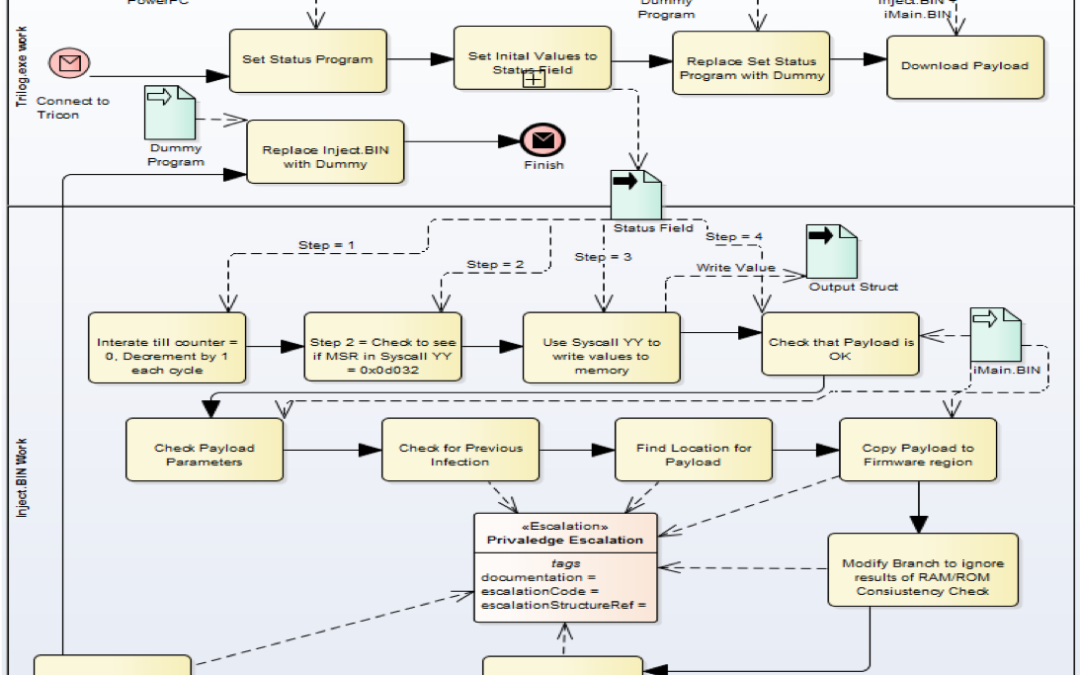
7 Feb 2018 | 2018, Attacks
Here are the three important things to take from this incident.
1) Schneider Electric set the new standard for ICS vendor response when a vendor’s system is attacked.
It’s hard not to compare Siemens’ response to Stuxnet with Schneider’s response to Triton. Siemens was pure denial and marketing spin; and not just in the early weeks, but literally for years. Stuxnet occurred over 7 years ago, and Siemens would likely do much better responding in 2018.
2 Jan 2018 | 2018, Podcast
Dale Peterson talks about the 2018 plans for this podcast, S4 and his consulting in this shorter 13-minute episode. He also talks about Digital Bond alumni spread throughout the industry and how this is likely the best time in ICS security for career opportunities and...


