2019 Articles

Shields Up Redux … Did They Ever Come Down?
The warnings went out after the US bombing of the Iranian nuclear facilities. Be prepared for an increased likelihood of an Iranian cyber attack. Shields Up! This is reasonable, perhaps even responsible to give this warning. The problem is there is no real guidance on...
Can We Share Information? (Log4j and CODESYS)
It started with Bryan Owen’s reply to a tweet. https://twitter.com/bryansowen/status/1523406471551094784?s=20&t=jFo6yRWaUeVYwCE2hAme6w Why after all these years of CODESYS security fails, although one could contend they are no worse than their peers, do so...
Hope In The ICS Security Workforce
We had the pleasure of hosting ~800 ICS security professionals in Miami South Beach last week at S4x22. While the record number of attendees was a good sign of the growing attention being paid to ICS security, it was the composition of the attendees that is even more...

Sprinting To Secure The US Power Grid
Last week a Bloomberg article covered the Biden Administration's plan for a 100-day sprint to secure the power grid. I'll comment on the three focus areas the article lays out and more broadly on 100-day efforts. Monitoring The Grid And Sending Data To The USG the...

Book Review: This Is How They Tell Me The World Ends by Nicole Perlroth
Short Review This is a book that an ICS security professional should give to friends and family to read so they know why they do what they do. Nicole guides the lay person through her compelling journey to understand the 0day market and its impact on the security of...
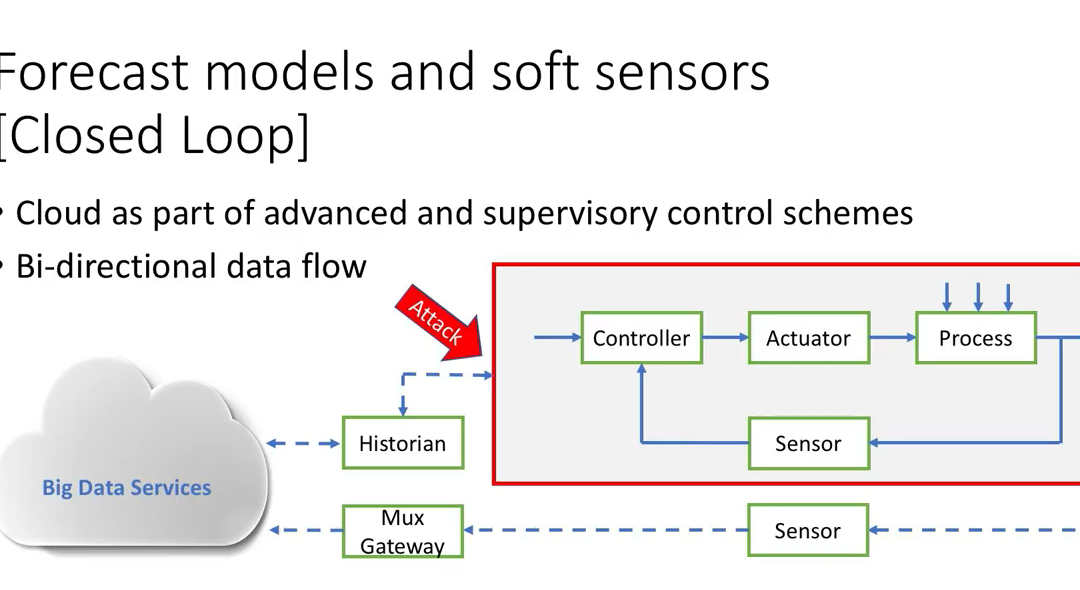
Securing Closed Loop ICS Cloud Services
Technology Is Available ... Is The Will There? Bryan Owen of OSIsoft defined, and perhaps coined, ICS cloud services as being open loop or closed loop. Securing open loop cloud services is simple. Just push the data out to the cloud for predictive maintenance,...
The Future of the ICS Product Market
Most of the activity in the ICS security product market has been around passive solutions that create asset inventories and detect cyber incidents. It is a bit astounding that the market and solutions will look almost completely different in two to five years than...

Podcast: Interview with Marina Krotofil
http://traffic.libsyn.com/unsolicitedresponse/2019-14_Marina_Krotofil.mp3 Marina Krotofil has been able to view the ICS security world from a number of perspectives. Beginning as an academic; working for an ICS vendor (Honeywell); working for an ICS security products...
Podcast: Sean McBride and ICS Cybersecurity Education
http://traffic.libsyn.com/unsolicitedresponse/2019-13_Sean_McBride.mp3 In this episode Dale interviews Sean McBride. Sean was on some of the earliest Unsolicited Response episodes when he was a Founder and Analyst with Critical Intelligence, the first ICS Threat Intel...
Podcast: An Interview with Patrick Miller
http://traffic.libsyn.com/unsolicitedresponse/2019-12_Miller.mp3 I took the opportunity to interview Patrick Miller while we were both in Sochi speaking at the Kaspersky KICS event. Patrick is a Founder and Managing Partner of Archer International, and he has been a...

Podcast: S4x19 Closing Panel
http://traffic.libsyn.com/unsolicitedresponse/2019-11_Closing_Panel.mp3 The S4 Closing Panel is always a candid discussion on where the community is in securing ICS, where we are succeeding and where need to do better. This year I was joined by Rob Lee of Dragos and...

Book Review: Security PHA Review
Rating: ★★★★☆ Tweet Length Review: Short and effective description of a process to add intentional cyber attacks to a Process Hazards Analysis (PHA). Includes basic process engineering examples that are highly useful for readers with an IT or IT security background....
Podcast: Rockwell Automation Cybersecurity
In this episode of the Unsolicited Response Podcast I interview Megan Samford and Rick Cherney of Rockwell Automation. http://traffic.libsyn.com/unsolicitedresponse/2019-10_Rockwell_Automation.mp3 We cover two main topics. First, we discuss how they are dealing with...
Forescout’s Strategy Post SecurityMatters Acquisition
An Interview With Brian Proctor http://traffic.libsyn.com/unsolicitedresponse/2019-9_Forescout.mp3 Forescout's acquisition of SecurityMatters for $113M in cash was the first major exit from the OT Detection Space (or broader passive monitoring market as you will hear...
Naiveté Redux: Preparation & Persistence Is Required To Attack ICS
"Gentlemen Do Not Read Each Others' Mail" There is a famous historical event in signals intelligence and cryptanalysis where the new and early successful US efforts in these areas were shut down, as covered by this article in the Atlantic. The Cipher Bureau was...

Podcast: An Interview With Jonathan Homer of DHS
In this episode, I interview Jonathan Homer, the Chief of the Industrial Control Systems Group / Hunt and Incident Response Team at DHS. http://traffic.libsyn.com/unsolicitedresponse/2019-8_DHS.mp3 We discuss: What changes will asset owners see with the creation of...
Podcast: ICS Firewall Market & Scoring SW/FW
An Interview with Eric Byres http://traffic.libsyn.com/unsolicitedresponse/2019-7_Eric_Byres.mp3 The ICS Detection Market has achieved almost all of the funding and attention the last two years, including my analysis. Last month Bayshore Networks announced and got...
ICS Detection Endgame
Hypothesis: The current ICS cyber incident detection solutions will not exist in three years. They are interim solutions, and competitors in the market need to identify and implement an endgame strategy as they continue to run very fast with the current solution. In a...

Podcast: Truth or Consequences
Consequence Based Techniques for ICS Risk Management http://traffic.libsyn.com/unsolicitedresponse/2019-6_Truth_or_Consequence.mp3 This recording is from a panel discussion on understanding and reducing the consequence side of the risk equation (risk = consequence *...
Podcast: Maritime Cybersecurity
In a recent article a researcher proclaimed it's "not hard for a hacker to capsize a ship at sea". This was quickly followed by the Viking Sky cruise ship having its engines shut off due to a sensor reading. Episode 2019-5: Maritime Cybersecurity Not knowing much...

Book Review: Secure Operations Technology
Summary: Andrew Ginter makes a plainspoken case for his view of what Secure Operations Technology (SEC-OT) means. The key point that diverges from the mainstream of ICS security thought is: Forbid firewalls as connection from ICS to IT networks – permit only...

Podcast: RSA Conference / ICS Village Report
I went back to the RSA Conference for the first time in over a decade. Here is my 25-minute report on the event for those considering attending or participating in the future. http://traffic.libsyn.com/unsolicitedresponse/RSA_2019-4.mp3 Includes: the...
Analysis of Dragos Platform Strategy … The Real Difference
What is Dragos? They have a diagram on their site that shows three business areas: Threat Intelligence Threat Operations Center (which are consulting services including incident response) Platform (their detection and response product) Dragos currently dominates...

An Interview with Robert Graham
I interviewed Robert Graham on the S4x19 Main Stage. Robert has an illustrious career in cyber security products including the creator of BlackIce and the first network IPS. We brought him to the S4 Stage for his contrarian views....
Organization and Expectations for ICS Detection
The cases being made in ICS owner / operator companies for the "best" organizational structure for ICS detection, and response, are heartfelt, well considered and often at great variance with one another. The case for Operational Technology (OT) SOC vs. Enterprise SOC...
ICS Security Patching: Never, Next, Now
This week we published the S4x19 video on three proposed revisions to the Common Vulnerability Scoring System (CVSS) for ICS vulnerabilities. It's worth a watch and hopefully it will be one more trigger for ICS-CERT to earn the "ICS" in their title and add ICS...
Is The Purdue Model Dead?
This episode of the Unsolicited Response Podcast features a discussion on the S4x19 Main Stage with Brad Hegrat, Joel Langill and Dale Peterson. The question: Is the Purdue Model Dead? http://traffic.libsyn.com/unsolicitedresponse/2019-2-Final-2-Purdue.mp3 The...

Post Game Analysis: S4 ICS Detection Challenge
How do you pick between 20+ ICS Detection and Asset Inventory solutions who are all claiming to be the best? The ICS Detection Challenge was designed to provide asset owner / potential customers with an unbiased technical comparison. S4x19 ICS Detection Challenge As...

4 Takeaways from 2018 … And Kicking Off 2019 With My S4x19 Mini Keynote
The first Unsolicited Response episode of 2019 is a shorter solo-sode. It begins with my four major takeaways from 2018: http://traffic.libsyn.com/unsolicitedresponse/Episode_19-1.mp3 Finally figuring out the OT / IT issue Consequence based risk reduction Detection...
20 Years of Digital Bond
In October 2018, Digital Bond turned 20. I thought before moving on to 2019 and starting our 21st year I’d reminisce a bit and thank the many employees over the past 20 years (see the list at the end of the article). Roger Collins and I started Digital Bond with $75K...
Article Archive By Year
Article Archive By Category
UPCOMING EVENTS
OTCEP ... 29 - 30 July 2025 in Singapore
One of the best OT Security events in Asia. Dale will be playing cowboy that week and will unfortunately miss it. Most of the rest of the OTCEP panel will be there on stage.
S4x26 ... 23 - 27 February 2026 in Miami South Beach
Save the date for S4x26. For the biggest and most future focused on ICS Security Event ... and likely our last time in Miami South Beach.
