2018 Articles
It’s Not OT v. IT
It's How Do We Best Build OT Teams & Programs My last post, Best Raw Material for an Operations Technology (OT) Team, received many comments on LinkedIn. A lot of the discussion devolved into the old IT v. OT discussion, partially due to my flippantly writing "IT...
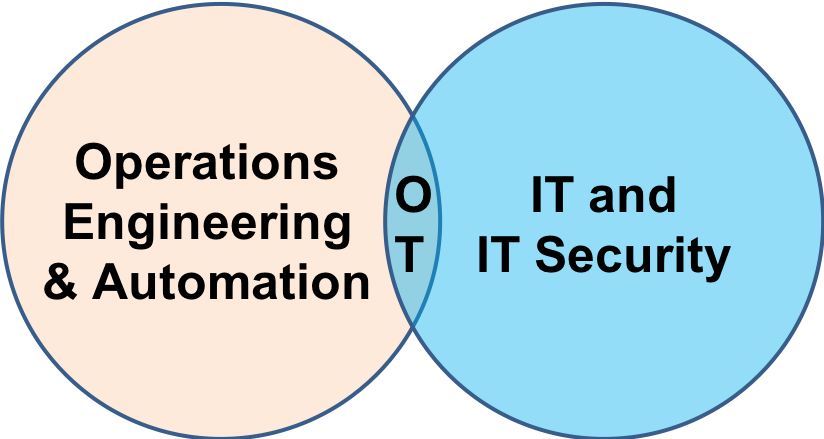
Best Raw Material for an OT Security Team
One of the topics we tackled in a panel at the Asia ICS Cyber Security Conference last week in Singapore was how best to grow the Operations Technology (OT) Security workforce. Early in his conference introduction Dan Ehrenreich showed a diagram similar to above with...
Podcast: Neighborhood Keeper for SMB Asset Owners
In this Unsolicited Response episode I interview Rob Lee of Dragos and Rob Smith of INL on a Department of Energy funded program called Neighborhood Keeper. The program attempts to provide threat detection and intelligence in an easy and affordable way to small and...
ICS Detection Market: Moving Fast & Facing Challenges
I've analyzed and made a number of predictions on the ICS Detection market over the past two years. The biggest surprise to me over the last six months has been speed of the market. The winners and losers are being largely determined in 2018 and will result in 10+...
Flawed ICS Mantras
I'm trying something a bit different in this short 22 minute episode. I rant about two flawed ICS mantras that are gaining traction and detract from useful discussions, and there is an overview of the S4x19 agenda and OnRamp training....
ICS / IIoT Market Segmentation Needed So We Can Communicate Effectively
There have been many events and data points that show even people knowledgeable in ICS and security are having difficulty communicating together because we have different views and experiences on what an ICS is. The latest example is Kaspersky's Threat Landscape for...
Unsolicited Response Podcast: Ralph Langner Interview on ICS Product Market
In this episode I speak with Ralph Langner of Langner Communications about the ICS Product Security Market. Ralph is famous for his work on Stuxnet, and he has done a lot of great work before and after Stuxnet. For the last two years he has set aside his decades of...
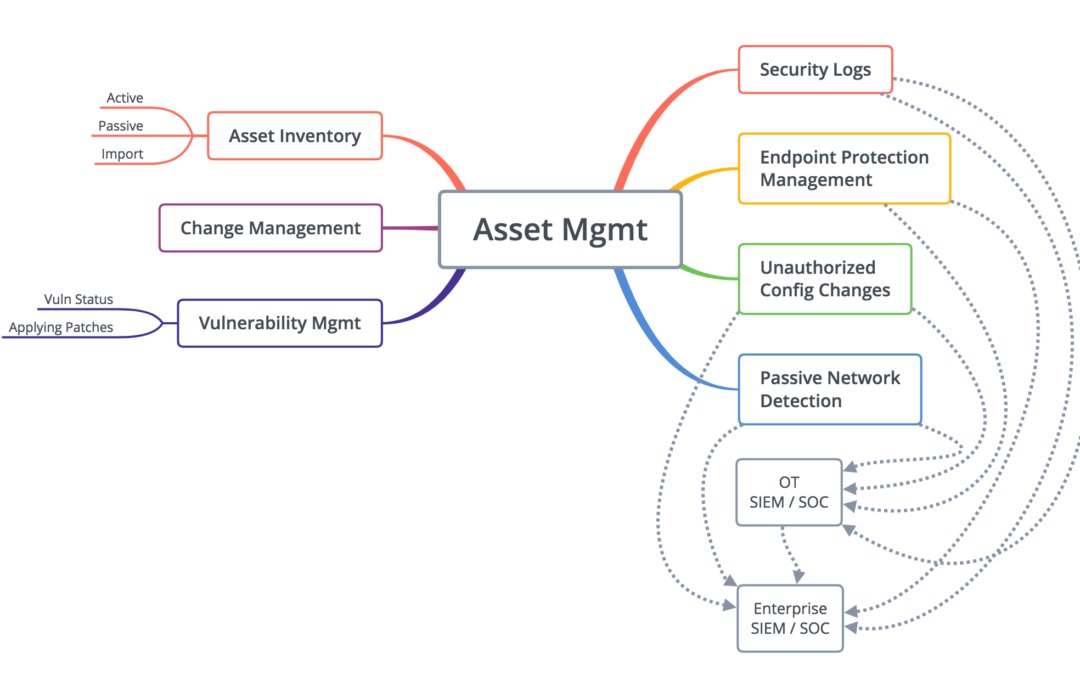
ICS Product Categories and Composition
Thinking Out Loud ... The ICS Detection market is new and highly competitive as covered in an early article. A question as interesting as who will be the winners in this market, is what the composition and capabilities of the winning solutions will be? The diagram...
Blake Sobczak of E&E News on Electric Sector Cybersecurity
Blake Sobczak, a reporter for Energy & Environment News, has been on fire lately with his coverage of electric sector cybersecurity. It seems like I'm consistently retweeting his stories and putting them into my Friday News & Notes email (are you subscribed?)....
Two Real Questions on the Weissian Crusade for Securing Process Sensors, Actuators and Drives
I like to call ICS security legend Joe Weiss the Paul Revere of the community. In the five years after the Sept 11th attacks, he was the most effective advocate and loudly carried the message that we have a huge risk that was not being addressed. He didn't stop in...
The Future of the ICS Cyber Security Detection Market
The ICS Cyber Security Detection market has 20+ vendors chasing this niche with most focused on passive network monitoring to create an asset inventory and identify cyber incidents. I've written on this developing market, interviewed participants on stage and in my...
Podcast: CCE with Andy Bochman of INL
Andy Bochman with INL joins me to discuss their Consequence-Driven, Cyber-Informed Engineering methodology (CCE). It is appealing because it places emphasis on the often neglected consequence part of the risk equation....

Michael Assante on the Podcast
Michael Assante is my guest for this episode. He has a storied career and recently won the RSA Conference Award for Excellence in Information Security. Mike was the VP/CSO of NERC, active at INL in the Aurora demonstration, led the development and implementation of the SANS ICS Security Training program, and even began working as CSO for an electric utility. We talk about driving change, what regulation would work, the lessons learned and failures of Aurora and much more.
Let’s Kill (Or Correct) The Term “Cyber Hygiene” In ICS
Hygiene was obviously selected by Andy and many others because it is easy to understand from its common usage, and who can possibly be against hygiene. Wash your hands before eating. Brush your teeth. Take a bath or shower. Change into clean clothes. Oh yes, we need cyber hygiene.
The easiest way to see the misuse and flaws in this term is that periodic wellness exams and vaccinations are not hygiene. Not everything a person does, and little a person has done for them, to maintain health is considered hygiene.
If we must keep the term cyber hygiene, then cyber hygiene should only include:
What’s Happening At ICS & IT Security Conferences
In the last two months Bryan Owen attended the SANS ICS Security Summit, DHS ICSJWG, RSA, OSIsoft's PI World, and LOGIIC (Oil/Gas/Gov consortium). Since most listeners like me aren't able to attend these events I thought we could find out what's happening from Bryan....
The Big Remaining Stuxnet Question
As we get ready to hear if President Trump will pull the US out of the Iran Nuclear Deal, it's worth revisiting the big remaining question and underreported story on Stuxnet: Why Did The US Government Not Care If Or Want Iran To Discover Stuxnet? Full credit for...
Press Coverage of ICS Security
This was a fun panel discussion on the S4x18 Main Stage with Kelly Jackson Higgins of Dark Reading and Jim Finkle of Reuters. http://traffic.libsyn.com/unsolicitedresponse/PressPanel.mp3 We covered a lot of grounds in a frank discussion including: Who is your reader?...
PODCAST: IATROGENICS – HARM DONE BY THE HEALER
Nassim Taleb discusses the concept of Iatrogenics in his book Antifragile. It is commonly applied to medicine, but Taleb applies it to the financial market and proposes it could be applied to other areas. We had a panel at S4x18 that dug into the issue of how to determine when security controls are doing more harm than good.
I was joined on stage by Jake Brodsky and Joel Langill. Jake is famously conservative when it comes to applying security controls, and Joel is a big proponent of some security controls that Jake would pass on. And all three of us are highly opinionated, so it made for an interesting discussion.

S4x18 Debate: Enterprise SOC or OT SOC?
This was a great debate from S4x18. Many owner / operators have an Enterprise Secure Operations Center (SOC), and they are considering how best to handle OT incident detection and response. There are two main approaches: 1. Add OT data and incident response capabilities to an Enterprise SOC or 2. Set up and run a SOC dedicated to the OT environment.

PODCAST: ICS DETECTION CHALLENGE INTERVIEWS
Dale Peterson interviews the ICS Detection Challenge Winner – Claroty and the runners up – Nozomi and Security Matters. They discuss where the competitors did well, how the products are likely to improve in the future, and what the future direction of the ICS product detection category is likely to be.
PODCAST: ICS DETECTION CHALLENGE ANALYSIS
The ICS Detection Challenge at S4x18 last January pitted Claroty, Gravwell, Nozomi and Security Matters in a competition to determine who could create the most complete asset inventory and who could do the best job detecting attacks through passive ICS network monitoring only. Dale Peterson and Eric Byres discuss the packets used in the test and analyze the results. What this product category can and cannot do. The last 15 minutes talking about the future of the ICS Detection product category.
MEDICAL CYBERSECURITY & DENSE VULNERABILITIES
After quickly agreeing that vulnerabilities in medical devices & software are dense, Dale Peterson and Josh Corman discuss where time and money should be spent on improving Medical Sector cybersecurity. Does the find and patch vulns make sense when the vulns are dense? Why does a hospital shut down for a week when a single application has an exploited vuln? How is the FDA doing in forcing change? What can we expect in the future. This and more in this episode.
ICS DETECTION CHALLENGE RESULTS – PART 2
The Asset Identification and Inventory results from the Challenge showed the potential of these solutions, but also the limitations due to maturity and a passive only approach. Claroty won the Asset Identification phase by identifying the largest number of assets (device type and vendor) with a score of 23, followed by Nozomi and Security Matters with a score of 20. Nozomi clearly provided the most detail in their asset inventory and was the only competitor to identify the key SCADA system. Security Matters did the best in identifying CVE’s for the asset inventory.
ICS DETECTION CHALLENGE RESULTS – PART 1
The Detection Phase of the ICS Challenge was won narrowly by Claroty (24) over Nozomi Networks (22) and Security Matters (22). Congratulations to the Claroty product and team. The final score was not as interesting as what was detected, what was missed, and conclusions about this product class. This post has five conclusions Dale pulled from the scoresheets and interviews, notes on the scoring methodology and deficiencies, and a chart showing the 19 incidents inserted into the packet capture.

DAN GEER INTERVIEW AT S4x18
I had the pleasure of interviewing Dan Geer on the S4x18 Main Stage for 30 minutes. He typically speaks from prepared papers, so an interview is a bit unique, and his papers provided plenty of topics and questions. We covered a wide range of issues including: Risk:...
TRITON TAKEAWAYS
Here are the three important things to take from this incident.
1) Schneider Electric set the new standard for ICS vendor response when a vendor’s system is attacked.
It’s hard not to compare Siemens’ response to Stuxnet with Schneider’s response to Triton. Siemens was pure denial and marketing spin; and not just in the early weeks, but literally for years. Stuxnet occurred over 7 years ago, and Siemens would likely do much better responding in 2018.
2018 PLANS: PODCAST, S4, CONSULTING & YOUR CAREER
Dale Peterson talks about the 2018 plans for this podcast, S4 and his consulting in this shorter 13-minute episode. He also talks about Digital Bond alumni spread throughout the industry and how this is likely the best time in ICS security for career opportunities and...
Article Archive By Year
Article Archive By Category
UPCOMING EVENTS
OTCEP ... 29 - 30 July 2025 in Singapore
One of the best OT Security events in Asia. Dale will be playing cowboy that week and will unfortunately miss it. Most of the rest of the OTCEP panel will be there on stage.
S4x26 ... 23 - 27 February 2026 in Miami South Beach
Save the date for S4x26. For the biggest and most future focused on ICS Security Event ... and likely our last time in Miami South Beach.
