2020 Articles

2020 Predictions – Right, Wrong & Pending
I made a number of predictions in 2020, some overlapping, in both my coverage of the detection market and as a feature of the monthly ICS security month in review episodes of the Unsolicited Response podcast. The predictions help with my analysis and hopefully...

Good News: 2020 Cyber Attacks On ICS Led To Very Small Consequences
Want something to feel good about as 2020 draws to a close? The impact of cyber attacks on ICS again this year, and every year since 2001, was very small. Extremely small. This includes financial impact, service impact, safety impact, environmental impact and any...

ICS Detection Product Integration with SIEM and Asset Management Solutions
At S4x19, a detection vendor had one of their customers on the Sponsor Stage to sing the praises of the product. In a moment of candor, the asset owner said the detection vendor's product was fantastic ... but they never looked at their management system because they...

ICS Detection Market Analysis – Part 2
Since I began seriously covering the ICS Detection Space in 2016, the products were quite similar. They passively listened on switch span ports and taps to: create an asset inventory (and provide vulnerability management but not asset management)detect attacks...

ICS Detection Market – Part 1
Part 1 looks at some of the major changes in the competitors focused primarily on the ICS detection market since the May update. Part 2 comes out next Tuesday and will map out where the competitors stand relative to each other and be a major change to the Tiers...

Security Outcomes in ICS
Cisco recently published their 2021 Security Outcomes Study. It is worth a close look. Not so much for the results and conclusions applicable to the enterprise, but the methodology is worth adopting for the ICS environment. It would be great if ARC or someone...
Grateful To Be In ICS Security
Happy Thanksgiving to my US readers. There is much to be thankful for if you are in the ICS security community. In my S4x20 keynote this past January, I contended that this is a great time to be in ICS security. https://youtu.be/IyLgMQEap44 Two months later, COVID...

Chris Krebs Firing Changes What?
Is It Time To Change Mission, Or At Least Expectations, For DHS? President Trump's firing of CISA Director Chris Krebs on Tuesday served no purpose except for petty vengeance. In just over two months he would not have to deal with Chris or any other appointees. At a...

Ransomware and ICS
Hype And Recovery A woman died in Germany concurrently with a ransomware attack on a hospital, and the media was flooded with articles about ransomware causing its first death. Wired's article this week, The Untold Story of a Cyber Attack, a Hospital and a...
Long Hidden ICS Cyber Risk, Not Increased Threat, Driving Disruption
I'm giving a keynote at an upcoming event, Fortinet's Secure OT 2020 on Nov 24-25, that has as its theme "Innovation Through Disruption. While I'll focus mostly on three ICS disrupting innovations in the next 1-3 years, I gave some thought on what is causing the...
Podcast: October Month In Review
Jason Nations and I go over October’s top three stories plus our Win, Fail and Prediction of the month.
Russian hackers charged, ICS vendor security services, and risk metrics.

Wanted: ICS Cloud Services Security Product
The technology exists. It just isn't being marketed and sold for this need. The majority of ICS related cloud services currently deployed are for predictive maintenance and performance analysis. These are 'open loop' services. Open loop in the sense that the cloud...
IEC 62443 Standards Are Ready For Their Close-Up
About every 18 months, I end up, as I am now, on a project where the asset owner wants to follow IEC 62443 security documents as closely as possible. As I re-read and use them, I'm struck by two things: There is a large amount of great content in the published and...
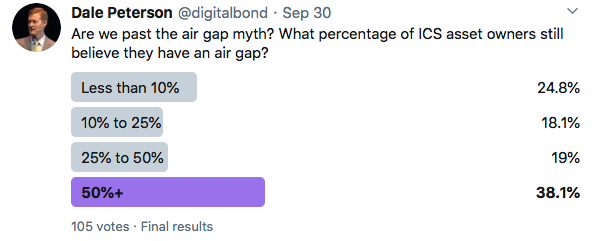
Podcast: September ICS Security Month In Review
The ICS Security Month in Review episodes cover two to three big stories from the month plus a win, a fail and a prediction. This month's stories include: S4x21's cancellation and S4x22 dates(7:01) Ransomware in ICS (12:30) SCIDMark and other ICS cyber incident...
Podcast: ATT&CK For ICS Evaluations
Detecting Triton Type Attacks In this episode I talk with Otis Alexander of MITRE about ATT&CK for ICS Evaluations. We begin with a discussion on ATT&CK and the ICS version of ATT&CK. If you are familiar with this, skip to 17:09 where we begin our...

Podcast: Splunk’s OT Security Add-On
Most of the OT Detection and Asset Management solutions have developed 'integrations' with SIEMs, with Splunk and QRadar being the most common. I put integrations in quotes because they did little more than push alerts and events to the SIEMs with little context. This...

Podcast: What OT Can Learn From IT
We hear it all the time. OT is different than IT, and IT doesn't understand OT. People argue about IT/OT convergence. In all these discussions I believe two things are true. OT doesn't really understand IT, and the similar, but not identical, requirements that mission...
Podcast: Interview with CISA Director Krebs on New Strategy
The US Department of Homeland Security CISA put out a new One CISA strategy document and an Alert in July. So I thought it would be a good time to talk with CISA Director Chris Krebs.
July – ICS Security Month in Review
Rob Caldwell of Mandiant joins Dale to discuss the top stories of July 2020 plus wins, fails and predictions on the Unsolicited Response podcast.
Podcast: P.W. Singer – Author of Burn In
P.W. Singer and August Cole recently published their second work of fiction – Burn In: A Novel About The Real Robotic Revolution. While it is a fiction, it uses over 300 examples of what might happen as robotics and revolution change the world over the next two decades.

ICS Security – Month In Review – June
Michael Toecker, Digital Bond alum and Founder of Context Industrial Security, joins Dale on the June ICS security month in review podcast. 3 big stories, plus Wins, Fails and Predictions.

Why Did Microsoft Acquire CyberX?
The rumors started in February and became reality this week. Microsoft acquired CyberX. The price is not a material event for Microsoft. It will never be officially released. A recent article claimed the price was $165M, and I predicted it would be...

Building & Using Digital Twins
An Interview with Mike Aylott of KBC There are many articles on digital twins that describe what they are and how they can help with predictive maintenance, efficiency studies, and other tasks of increasing interest and value. On the security side digital twins...

Panama Canal: 3 Lessons
I just finished David McCullough's book on the building of the Panama Canal. At 700-pages it's a bit of a slog so I can't recommend it, and yet there were so many fascinating stories and details. Here are my top three. Amazing Early Example Of A Control System...

Podcast: Matt Wyckhouse of FiniteState
I interview Matt Wyckhouse, Founder and CEO of Finite State. They have a solution that tests ICS firmware to help with supply chain issues. We talk about starting a company, VC’s, firmware testing and business models.

No Limits: More Than Moving To Remote and Virtual
This January in Miami South Beach I announced the theme of S4x21 the following January: No Limits! We selected No Limits because our plan was to rethink every element of the event, unrestricted by what we did in the past or conference norms, AND we were going to place...

ICS Security – Month In Review – May
I've been wanting to start adding a month in review episode to the Unsolicited Response podcast ever since I became a fan of the Pivot podcast. Have a looser conversation on the stories of the month and then predictions, wins and fails with someone in the ICS security...

ICS Detection Market Q2 Update
Part 2: Acquirers, Enterprise Vendors and Tier 3 See Part 1: COVID 19 Impact, Tier 2 and Tier 1 Analysis, and Valuation First the updated chart and then the analysis below. You will see big changes in Tiers 2 & 3. Funding data comes from Crunchbase. Acquirers and...

Podcast: COVID-19 Impact on ICS Careers, Companies and S4x21
This is a shorter solo-sode rather than the typical interview format. I wanted to hold off on making any COVID-19 analysis or comments until the rawness and shock of the event had subsided somewhat....

ICS Detection Market Q2 Update
Part 1 - COVID 19 Impact, Tier 2 and Tier 1 Analysis, and Valuation My previous ICS Detection Market Update was in November, 2019. A lot has changed. Part 2 next week will include analysis of the acquirers, enterprise vendors and Tier 3. As always, huge respect for...

Podcast: S4x20 Closing Panel
Ralph Langner of Langner, Inc. and Zach Tudor of INL join me on the S4x20 Closing Panel. This is always one of the most fun and highly rated session at S4. https://traffic.libsyn.com/secure/unsolicitedresponse/2020-11_S4x21_Closing_Panel.mp3 We cover a lot of ground...

Interview with Inventor & Legend Ed Schweitzer
This podcast is the audio from my S4x20 Main Stage interview with electric sector and ICS legend Ed Schweitzer. He was the perfect person to interview related to the event theme: Create The Future in OT and ICS security. It's a wide ranging and fun interview. (Ed has...

Podcast: Interview with Bryan Owen of OSIsoft
Winner of the 2020 Michael J. Assante ICS Security Lifetime Achievement Award Bryan and I were scheduled to go skiing prior to ICSJWG in Park City. With that squashed we decided to record a podcast instead. Bryan and I begin with what winning the Michael J. Assante...
Podcast: Tenable’s OT Strategy with Marty Edwards
Marty Edwards has worked for an ICS asset owner, INL, DHS, ISA and late last year he made the move to a security product vendor, Tenable. This happened at the same time that Tenable acquired Indegy for $78M, indicating they are serious about OT security space. I talk...
Podcast: Board of Directors Role in ICS Security with Thomas Parenty
A big challenge facing any team trying to deal with OT and ICS cyber risk is getting executive leadership and the Board of Directors support and leadership on this issue. The problems that arise tend to be related to communication styles, understanding of what is...
Podcast: ICS Threat Intel with Sergio Caltagirone
Sergio began his career doing threat intelligence in the US Government's NSA and now is the VP of Threat Intel at Dragos. We focus in this episode on where the data for threat intel is obtained, how the threat intel product is created, and how it should be used by an...
Solarium Report Eclipsed By Pandemic
And This Is A Good Thing The long awaited U.S. Cyberspace Solarium Commission Report came out and received very little attention given more pressing pandemic events. And this is a good thing. I'll provide some critique and then, to be fair, provide my...

Podcast: An Interview with Andy Greenberg – Author of Sandworm
In this episode Dale Peterson interviews Sandworm author and Wired Senior Writer Andy Greenberg on the S4x20 Main Stage. They focus on the ICS issues in the story. http://traffic.libsyn.com/unsolicitedresponse/20-5_Andy_Greenberg.mp3 The discussion includes: What led...

Create The Future Of OT & ICS Security
Note: This week has been full of depressing events, and our main hope is for everyone to get through this safely. The future will be brighter, and let's use some of this time of isolation to figure out what we want and start...
It Won’t Work In ICS … Until It Does
My most vivid early experience with 'it won't work in ICS' was in 2006. We had received a DHS research contract to develop Snort intrusion detection signatures and preprocessors for ICS protocols (originally Modbus and DNP3). I was presenting the working solution at a...

Kelly Jackson Higgins Interviews Dale
The tables are turned in this episode of the Unsolicited Response podcast with Kelly Jackson Higgins of Dark Reading interviewing Dale in the S4x20 Green Room. Kelly has been coming to S4 and covering the ICS security space for over seven years, and this experience...
Everyone Can Play In OT / ICS Security
Seth Godin wrote this in a recent daily blog post: You Can't Say You Can't Play. Lenny Levine was a great kindergarten teacher. And he ran his class by this one rule. It means that if another kid comes along, you need to include them in your game. That's it. This is...

Unsolicited Response – The Cabana Sessions with Reid Wightman, Stephan Hilt and Lord Remorin
I spoke with two Digital Bond alumni and Lord Remorin at the S4x20 Cabana Sessions about a wide ranging set of technical topics. http://traffic.libsyn.com/unsolicitedresponse/2020-3_Cabana_Sessions.mp3 Reid Wightman, Principal Vulnerability Analyst at Dragos What he...
Prediction: ICS Incident Response Services Will Be Key Criteria For ICS Detection Product Selection
I've made three predictions to date in my analysis of the ICS detection market, and now I'm adding a fourth. The first three are: The 'we only do passive, active is dangerous' mantra will be replaced as asset owners realize adding legitimate ICS active requests...

Megan Samford – ICS4ICS
Dale Peterson interviews Megan Samford of Rockwell Automation in the S4x20 Green Room. The main topic is Megan's idea of an Incident Command System for Industrial Control Systems (ICS4ICS). While working for the State of Virginia, Megan was active with and saw first...
2019 – What Changed in ICS Security?
Increase In Community Size/Talent and "The Dip" In December I was preparing my 15-minute mini-keynote to kick off for S4x20 in January, and I was having a hard time finding anything truly unique or significant change in ICS security in 2019. So I asked eight people I...

Interview with CISA Director Krebs
We created a lot of great content at S4x20, including a number of interviews that we will be releasing in the podcast. This episode is my ~30 minute interview with DHS CISA Director Chris Krebs in the S4x20 Green Room....
Article Archive By Year
Article Archive By Category
UPCOMING EVENTS
OTCEP ... 29 - 30 July 2025 in Singapore
One of the best OT Security events in Asia. Dale will be playing cowboy that week and will unfortunately miss it. Most of the rest of the OTCEP panel will be there on stage.
S4x26 ... 23 - 27 February 2026 in Miami South Beach
Save the date for S4x26. For the biggest and most future focused on ICS Security Event ... and likely our last time in Miami South Beach.
